今年再次参加了浙江省赛,今年是第二次参赛了,与队内的web和bin大手子一起组了队,这次预赛的成绩还是不错的,拿到第6,决赛已经稳了。这篇blog就记录一下赛中解的Crypto题水一篇。
小小数学家 #
看到题目内容和附件,就直接按照描述所说,计算一坨算式即可,直接eval()了
probs = open('flag.txt').readlines()
flag = []
for prob in probs:
prob = prob[:-3]
flag.append(int(eval(prob)))
print(bytes(flag))
EC_Party-III #
题目关键代码
p = getPrime(384)
q = getPrime(384)
n = p*q
d = getPrime(80)
e = inverse_mod(d, ord_p*ord_q)
直接就想到了wiener attack,在EC中$Order(p) = p+1+\alpha$,alpha是一个小于$2\sqrt{p}$的数,本来是想要调一下的,但是发现不用改直接连分数就出了
from sage.all import *
from Crypto.Util.number import getPrime, long_to_bytes
pk = [10517482889776460226798449006280081167663671198448544453304563030553066300585088657159799516828057458092448853052920, 10402402380108575947733278581108880071660185906203575453837669489513650182676772750843558327746184945922314875098996, 452239510514900186933709062848646640558105660312444312121851933676754687850508865659206624803226663304812888272594694285123823218948165607478144589871322148031514596122654196640778853480169180864412134209693877604844174450602155353, 137939931394124279393027766586199451754893501053862574760060288577053514723631473985259186063729745515767167268309839903521149677958518517988564142828176577685619561913731155508981456507557881596602396073589127827579264760182112015, (312312975924665463422872243489714243976133330669934414246404507993066820310886215600585539115436654843078716170526368558972800117033427241194242498913898005160762151892979826292737941332916578310350510245475526522735894588645243659, 422891099305786578397746684898210811095359530216631541482542541898542508551347882962281401572399110483550691802487377837504493122807091311281569558317360479103461652558448871769150783477147866528115922507893061101403528629595165327)]
a, b, n, e, C = pk
E = EllipticCurve(Zmod(n), [a, b])
C = E(C)
print(C)
def attack1(N, e):
convergents = continued_fraction(ZZ(e) / ZZ(N)).convergents()
for c in convergents:
k = c.numerator()
d = c.denominator()
M = d*C
flag = long_to_bytes(int(M.xy()[0]))
try:
print(flag[:-16].decode())
except:
continue
print(attack1(n, e))
基础数论 #
from secret import x,y
from hashlib import md5
from sympy import isprime,nextprime
p = x**2 + y**2
assert isprime(p) and x*y > 0
print(p)
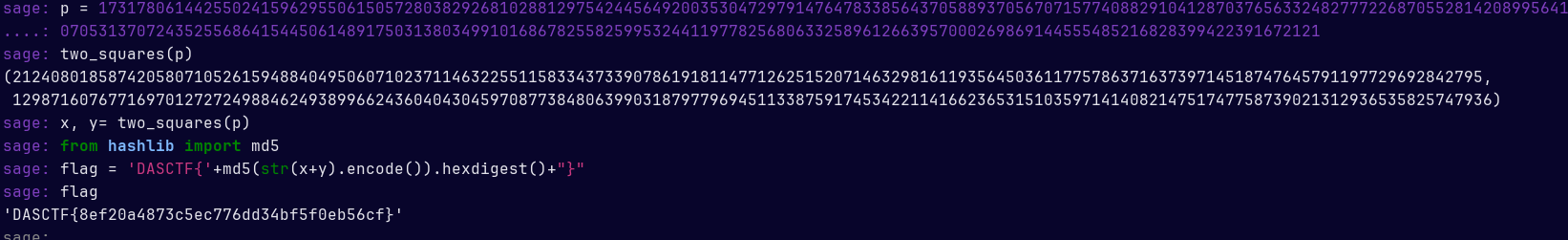
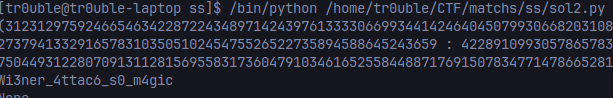
两数平方和,Crypto CTF 有过一样的题,sagemath two_squares()直接秒